 Ethical Hacking:
Ethical Hacking is the methodology used to locate the weaknesses and drawbacks of Information Systems or a Computer over a network. Under Ethical Hacking, the person gets a legal authentication to access the data and identify the potential threats. As a result, Ethical Hackers take necessary steps to minimize the possibilities of identified threats and initiate actions to ensure there are no loopholes in the existing IT infrastructures.
Required Skills of an Ethical Hacker:
Ethical Hacking is becoming a need of every organization that wishes to keep its data safe and secure from unethical attacks. Ethical Hackers prove to be a boon to such organizations, but every Ethical Hacker needs a deep understanding of few skills that contribute in effective implementation of Ethical Hacking. Therefore, an Ethical Hacker should have knowledge of the following:
>> Routers
>> Microsoft-based systems
>> Linux
>> Mainframes
>> Firewalls
>> Network Protocol
>> Project Management
An Ethical Hacker can have an expertise in either of the above or may be more, as Security tests under Ethical Hacking are done by a team of individuals.
Modes of Ethical Hacking:
After gaining the skillset of Ethical Hacking, comes its implementation. Every organization, these days has a fear of getting hacked in numerous ways, hence the Ethical Hackers try every possible manner to check out the certainties of unethical attack on IT infrastructure. Following are different modes of Ethical Hacking:
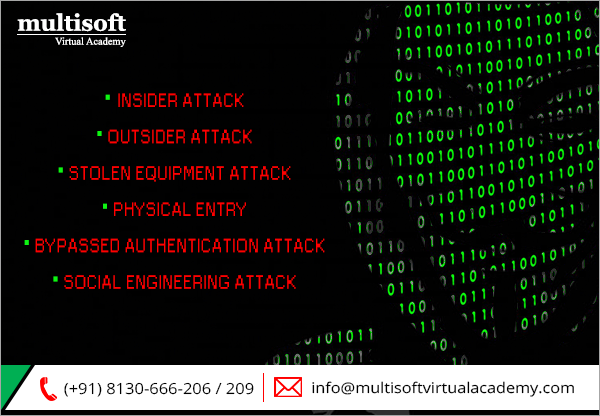
Insider attack:
This type of hack includes identifying the types and activities of attacks that are carried out on the system by the Ethical Hacker who has an authorized access to the organization’s network.
Outsider attack:
This hack finds out the type of attacks that are instigated across the Internet. The aim is to target HTTP, SMTP, SQL or other available services.
Stolen equipment attack:
This type of hack is focused on physical attack, as its target is the organization’s equipment. Its goal includes targeting CEO’s laptop or backup tapes of the organization to extract confidential information, usernames, and passwords.
Physical entry:
This hack is used to test physical controls of the organization. Under this hacking, the systems like locks, doors, alarms, gates, CCTV, and guards are tested to check whether they can be bypassed or not.
Bypassed authentication attack:
The motive of this hack is to check wireless access points (WAP) and modems. It analyzes if the systems have the required authentication controls and cannot be bypassed. The Ethical Hacker probes that upto what level the systems can be hacked.
Social engineering attack:
This type of hacking doesn’t focus on physical or technical access. It targets to reach the organization’s employees and tries to manipulate them to acquire confidential information. Proper implementation of procedures, policies, and rules can help the organization to stay safe from this hacking attack.
Ethical Hacking domain has a wide scope and a bright future for the aspirants. The ones who wish to explore more about it can opt for a formal training to get a deep insight of this domain.
Ethical Hacking:
Ethical Hacking is the methodology used to locate the weaknesses and drawbacks of Information Systems or a Computer over a network. Under Ethical Hacking, the person gets a legal authentication to access the data and identify the potential threats. As a result, Ethical Hackers take necessary steps to minimize the possibilities of identified threats and initiate actions to ensure there are no loopholes in the existing IT infrastructures.
Required Skills of an Ethical Hacker:
Ethical Hacking is becoming a need of every organization that wishes to keep its data safe and secure from unethical attacks. Ethical Hackers prove to be a boon to such organizations, but every Ethical Hacker needs a deep understanding of few skills that contribute in effective implementation of Ethical Hacking. Therefore, an Ethical Hacker should have knowledge of the following:
>> Routers
>> Microsoft-based systems
>> Linux
>> Mainframes
>> Firewalls
>> Network Protocol
>> Project Management
An Ethical Hacker can have an expertise in either of the above or may be more, as Security tests under Ethical Hacking are done by a team of individuals.
Modes of Ethical Hacking:
After gaining the skillset of Ethical Hacking, comes its implementation. Every organization, these days has a fear of getting hacked in numerous ways, hence the Ethical Hackers try every possible manner to check out the certainties of unethical attack on IT infrastructure. Following are different modes of Ethical Hacking:
Insider attack:
This type of hack includes identifying the types and activities of attacks that are carried out on the system by the Ethical Hacker who has an authorized access to the organization’s network.
Outsider attack:
This hack finds out the type of attacks that are instigated across the Internet. The aim is to target HTTP, SMTP, SQL or other available services.
Stolen equipment attack:
This type of hack is focused on physical attack, as its target is the organization’s equipment. Its goal includes targeting CEO’s laptop or backup tapes of the organization to extract confidential information, usernames, and passwords.
Physical entry:
This hack is used to test physical controls of the organization. Under this hacking, the systems like locks, doors, alarms, gates, CCTV, and guards are tested to check whether they can be bypassed or not.
Bypassed authentication attack:
The motive of this hack is to check wireless access points (WAP) and modems. It analyzes if the systems have the required authentication controls and cannot be bypassed. The Ethical Hacker probes that upto what level the systems can be hacked.
Social engineering attack:
This type of hacking doesn’t focus on physical or technical access. It targets to reach the organization’s employees and tries to manipulate them to acquire confidential information. Proper implementation of procedures, policies, and rules can help the organization to stay safe from this hacking attack.
Ethical Hacking domain has a wide scope and a bright future for the aspirants. The ones who wish to explore more about it can opt for a formal training to get a deep insight of this domain.
| Start Date | Time (IST) | Day | |||
|---|---|---|---|---|---|
| 07 Mar 2026 | 06:00 PM - 10:00 AM | Sat, Sun | |||
| 08 Mar 2026 | 06:00 PM - 10:00 AM | Sat, Sun | |||
| 14 Mar 2026 | 06:00 PM - 10:00 AM | Sat, Sun | |||
| 15 Mar 2026 | 06:00 PM - 10:00 AM | Sat, Sun | |||
|
Schedule does not suit you, Schedule Now! | Want to take one-on-one training, Enquiry Now! |
|||||